Lantronix SpiderDuo: Difference between revisions
No edit summary |
No edit summary |
||
| (10 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[File:Lantronix_SpiderDuo.jpg|480px|thumb|right|Lantronix_SpiderDuo]] | [[File:Lantronix_SpiderDuo.jpg|480px|thumb|right|Lantronix_SpiderDuo]] | ||
=Details= | |||
Nice KVM over IP with USB port for remotely connecting virtual media. The current price as of 2021-02-05 is $559 although I think I got it for less than that years ago. There are more and cheaper solutions out there today, but this still works. | |||
* [https://www.lantronix.com/products/lantronix-spiderduo/ Manufacturer Page] | |||
* [https://www.lantronix.com/wp-content/uploads/pdf/Spiders_UG.pdf Documentation] | |||
=Modern Open Source Alternatives= | |||
* [https://www. | For a long time there were no alternatives to devices like this, but now finally there's a cheap DIY project that can accomplish the same thing for much cheaper: [https://github.com/pikvm Pi-KVM Project] (Open and cheap DIY IP-KVM based on Raspberry Pi). It only costs between $30 and $100 for parts! | ||
* | <br> | ||
Resources: | |||
* [https://www.youtube.com/watch?v=dTchVKxx7Fo&feature=youtu.be Pi-KVM - DIY CHEAP Raspberry Pi KVM over IP Prototype Version 3 Review!] on YouTube | |||
* [https://www.youtube.com/watch?v=xCL5AS0t5Is&t=310s Pi-KVM - Raspberry Pi Zero W Installation and Review] on YouTube | |||
=Firmware= | |||
...but | On 2020-06-30, version: 4.2.0 (Build 38135) was released. I have confirmed that this version supports the HTML 5 KVM mode. | ||
* See release notes here: [ftp://ftp.lantronix.com/pub/spider/4.2/spider-v4.2-38135_2020-06-30-release_notes.txt spider-v4.2-38135_2020-06-30-release_notes.txt] | |||
* Download here: [ftp://ftp.lantronix.com/pub/spider/4.2/spider-v4.2-38135_2020-06-30.zip spider-v4.2-38135_2020-06-30.zip] | |||
On 2020-02-26, version: 4.1.2 (Build 38134) was released. The release notes imply that this version supports the HTML 5 KVM mode but I have not tested it. | |||
* See release notes here: [ftp://ftp.lantronix.com/pub/spider/4.1.2/spider-v4.1-38134_2020-02-26-release_notes.txt spider-v4.1-38134_2020-02-26-release_notes.txt] | |||
* Download here: [ftp://ftp.lantronix.com/pub/spider/4.1.2/spider-v4.1-38134_2020-02-26.bin spider-v4.1-38134_2020-02-26.bin] | |||
On 2019-05-15, version 3.00.31 (Build 38120) was released. This version did not support HTML 5 KVM mode. | |||
* See release notes here: [ftp://ftp.lantronix.com/pub/spider/3.00.31/spider-v3.0-38120_2019-05-15-release_notes.txt spider-v3.0-38120_2019-05-15-release_notes.txt] | |||
* Download here: [ftp://ftp.lantronix.com/pub/spider/3.00.31/spider-v3.0-38120_2019-05-15.bin spider-v3.0-38120_2019-05-15.bin] | |||
On 2018-12-17, version 04.00.08 (Build 38118) was released. This was the first version to support HTML 5 KVM mode, but the download was taken down from the Lantronix website shortly afterwards. [https://www.reddit.com/r/homelab/comments/awyid6/lantronix_spider_ipkvm_now_supports_html5/ See this reddit thread for details]. Nobody really knows what, if anything, is wrong with this firmware. It has been made available by a third party for posterity. The links below are not directly provided by Lantronix. | |||
* See release notes here: [https://mega.nz/folder/higjRCoJ#p2kDrKlPccw0ZtGBn8SDjg/file/Q6wzhaDD spider-v4.0.8-38118_2018-12-17_User_Release_Notes.txt] | |||
* Download here: [https://mega.nz/folder/higjRCoJ#p2kDrKlPccw0ZtGBn8SDjg/file/p6gRDYCL spider-v4.0.8-38118_2018-12-17.bin] | |||
=Installing an SSL certificate= | |||
Unfortunately, this little appliance doesn't allow you to simply upload an SSL certificate. Rather, you need to create a certificate signing request (CSR) and send that to your SSL certificate provider / authority. | |||
<br><br> | |||
Step 1: Generate a certificate signing request on the Spider Duo portal. If your hostname for your lantronix spider duo is <tt>spider</tt>, you would go here: https://spider/cert.asp | |||
<br>[[File:Spider duo cert page.png|800px|Lantronix_SpiderDuo]] | |||
<br> | |||
Fill out all fields and change the key length to the highest available (currently only 2048). Then click the "Create" button. | |||
<br><br> | |||
Step 2: Download the CSR file and save to <tt>csr.txt</tt> | |||
<br><br> | |||
Step 3: Use the [https://certbot.eff.org/ certbot] tool to create the certificate. This will require validation of the fact that you control the domain (common name) of the certificate. In this example, I use the webroot option and the common name of the certificate is <tt>certificate-example.mydomain.com</tt>: | |||
jeremy@latitude /tmp/cert $ DIR_CONFIG=./config | |||
jeremy@latitude /tmp/cert $ DIR_WORK=./work | |||
jeremy@latitude /tmp/cert $ DIR_LOGS=./logs | |||
jeremy@latitude /tmp/cert $ mkdir $DIR_CONFIG $DIR_WORK $DIR_LOGS | |||
jeremy@latitude /tmp/cert $ certbot certonly --cert-path cert.pem --key-path key.pem --csr csr.txt --config-dir $DIR_CONFIG --work-dir $DIR_WORK --logs-dir $DIR_LOGS | |||
Saving debug log to /tmp/cert/logs/letsencrypt.log | |||
How would you like to authenticate with the ACME CA? | |||
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - | |||
1: Spin up a temporary webserver (standalone) | |||
2: Place files in webroot directory (webroot) | |||
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - | |||
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 | |||
Plugins selected: Authenticator webroot, Installer None | |||
Enter email address (used for urgent renewal and security notices) (Enter 'c' to | |||
cancel): youremail@mailprovider.com | |||
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - | |||
Please read the Terms of Service at | |||
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must | |||
agree in order to register with the ACME server at | |||
https://acme-v02.api.letsencrypt.org/directory | |||
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - | |||
(A)gree/(C)ancel: A | |||
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - | |||
Would you be willing to share your email address with the Electronic Frontier | |||
Foundation, a founding partner of the Let's Encrypt project and the non-profit | |||
organization that develops Certbot? We'd like to send you email about our work | |||
encrypting the web, EFF news, campaigns, and ways to support digital freedom. | |||
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - | |||
(Y)es/(N)o: N | |||
Performing the following challenges: | |||
http-01 challenge for certificate-example.mydomain.com | |||
Input the webroot for certificate-example.mydomain.com: (Enter 'c' to cancel): /var/www/html | |||
Waiting for verification... | |||
Cleaning up challenges | |||
Server issued certificate; certificate written to /tmp/cert/cert.pem | |||
Cert chain written to 8 | |||
Cert chain written to 9 | |||
<br><br> | |||
Step 4: Upload the <tt>cert.pem</tt> file to the Spider Duo portal. | |||
<br><br> | |||
Step 5: Rest easy that there's no man in the middle. | |||
=SSH Access= | |||
<pre> | |||
sysadmin@192.168.1.96's password: | |||
Welcome to the Lantronix SLSLP | |||
Firmware: version 040200, build 38135 | |||
Last login: Thu Jan 1 12:18:43 1970 from 192.168.1.109 | |||
Current time: Thu Jan 1 21:43:54 1970 | |||
For a list of commands, type 'help' | |||
[sysadmin@192.168.1.96]> help | |||
SLS Command Line Help | |||
--------------------- | |||
For more information on a command, type 'help <command>' | |||
For example, 'help show history'. | |||
For general CLI help, type 'help command line'. | |||
set datetime|device|group|history|network|oem|power|security|serial| | |||
sshkey|user|vip | |||
show datetime|device|group|history|network|oem|power|security|serial| | |||
sshkey|sysconfig|user|vip | |||
connect serial|wakeonlan | |||
diag ping|ping6 | |||
usbhost disk | |||
admin config|reboot|reset|version | |||
logout terminates CLI session | |||
[sysadmin@192.168.1.96]> | |||
[sysadmin@192.168.1.96]> | |||
[sysadmin@192.168.1.96]> set datetime ? | |||
Date/Time Command Synopsis | |||
-------------------------- | |||
Set the date/time or UTC offset: | |||
set datetime <one parameter> | |||
Parameters: date <MMDDYYhhmm[ss]> | |||
utcoffset <offset string> | |||
MMDDYYhhmm[ss]: | |||
MM: 1-12 DD: 1-31 YY: 00-99 | |||
hh: 0-23 mm: 0-59 ss: 0-59 | |||
Offset string: | |||
-11h, -10h, -9h, -8h, -7h, -6h, -5h, -4h, -3h, -2h, -1h, | |||
+/-0h, | |||
+1h, +2h, +3h, +4h, +5h, +6h, +7h, +8h, +9h, +10h, +11h, +12h. | |||
(Note: Select only one offset as shown above) | |||
Show the date/time and UTC offset: | |||
show datetime | |||
[sysadmin@192.168.1.96]> set device ? | |||
Device Command Synopsis | |||
--------------------- | |||
Display device information: | |||
show device | |||
show device all | |||
show device name [name <Device Name>] | |||
show device [index <Index Number>] | |||
Configure device information: | |||
set device add|edit <Device Name> | |||
macaddress <MAC Address> | |||
[<parameters>] | |||
Parameters: ipaddress <IP Address> | |||
password <Password> | |||
MAC address must be in hex format: 'XX:XX:XX:XX:XX:XX' | |||
set device delete <Device Name> | |||
[sysadmin@192.168.1.96]> set group ? | |||
User Group Command Synopsis | |||
--------------------------- | |||
Configure user group for users who login to SLS. | |||
set group add|edit <Group Name> [<parameters>] | |||
set group delete <Group Name> | |||
Parameters: permissions <Permission List> | |||
Note: See 'help group permissions' for information on groups rights. | |||
Display group information: | |||
show group [name <Group Name>] | |||
show group [index <Index Number>] | |||
Note: [Group of 'None (username)'] indicates that user was created | |||
without defining a group, and permissions will be assigned | |||
specifically to the user. In order to specify a group of | |||
this type "None", use '@username' as the name parameter. | |||
[sysadmin@192.168.1.96]> set history ? | |||
History Command Synopsis | |||
------------------------ | |||
Clears the CLI command history: | |||
set history clear | |||
Displays the 100 most recent CLI commands: | |||
show history | |||
[sysadmin@192.168.1.96]> set network ? | |||
Network Command Synopsis | |||
------------------------ | |||
Configures network setting: | |||
set network basic <parameters> | |||
Parameters: | |||
dns1 <IP Address> | |||
dns2 <IP Address> | |||
gateway <IP Address> | |||
hostname <Host Name> | |||
ipaddr <IP Address> | |||
ipv6 <enable/disable> | |||
ipv6addr <IPv6 Address/Prefix> | |||
mask <Mask> | |||
state <dhcp|bootp|static> | |||
set network misc <parameters> | |||
Parameters: | |||
bwlimit <8-10000 kbit/s> | |||
httpsports <TCP Port> | |||
httpport <TCP Port> | |||
proxy <enable/disable> | |||
proxyhost <IP Address> | |||
proxyport <TCP Port> | |||
telnet <enable/disable> | |||
telnetport <TCP Port> | |||
setupprotocol<enable/disable> | |||
ssh <enable/disable> | |||
sshport <TCP Port> | |||
set network interface <parameters> | |||
Parameters: | |||
mode <auto|10mbit-half|100mbit-half|10mbit-full|100mbit-full> | |||
Display network parameter settings. | |||
show network all | |||
show network basic | |||
show network misc | |||
show network interface | |||
To clear IPV4 address, set ipv4 address to '0.0.0.0' | |||
To clear IPV6 address, set ipv6 address to '::' or '::/128' | |||
[sysadmin@192.168.1.96]> set oem ? | |||
OEM Customization Command Synopsis | |||
---------------------------------- | |||
Configure OEM customization parameters. | |||
Change product/company specific information on the web interface. | |||
Set OEM parameters: | |||
set oem <one or more parameters> | |||
Parameters: [product <Product Name>] | |||
[company <Company Name>] | |||
[copyright <Copyright>] | |||
[url <URL>] | |||
[title <Title>] | |||
[Examples] | |||
set oem product MyKVM company MyCompany | |||
Set product name 'MyKVM' and company name 'MyCompany' | |||
Display OEM settings: | |||
show oem | |||
[sysadmin@192.168.1.96]> set power ? | |||
Power Command Synopsis | |||
---------------------- | |||
Configure Power Control Unit (PCU) parameters. | |||
Set PCU parameters: | |||
set power <parameters> | |||
Parameters: [state <on/off>] | |||
Display Power Control Unit status and settings: | |||
show power | |||
[sysadmin@192.168.1.96]> set security ? | |||
Security Command Synopsis | |||
------------------------- | |||
Set security parameters: | |||
set security <one or more parameters> | |||
Parameters: [forcehttps <enable|disable>] | |||
[singlelogin <enable|disable>] | |||
[kvmencryption <off/try/force>] | |||
[screenshot <enable|disable>] | |||
[directkvm <enable|disable>] | |||
Show security settings. | |||
show security | |||
[sysadmin@192.168.1.96]> set serial ? | |||
Serial Port Command Synopsis | |||
---------------------------- | |||
Set active serial mode: | |||
set serial mode passthrough | |||
set serial mode config | |||
Set serial port parameters for each mode: | |||
set serial mode passthrough|config [<parameters>] | |||
Parameters: [baud <300-115200>] | |||
[databits <7|8>] | |||
[stopbits <1|2>] | |||
[parity <none|odd|even>] | |||
[flowcontrol <none|xon/xoff|rts/cts>] | |||
Show serial port settings | |||
show serial | |||
[sysadmin@192.168.1.96]> set sshkey ? | |||
SSH Key Command Synopsis | |||
------------------------ | |||
Import SSH key (OpenSSH format): | |||
set sshkey import <copypaste> | |||
Note: RSA keys must be 1024 bits. | |||
Import SSH key (OpenSSL format) : | |||
set sshkey import <copypaste> format <openssl> | |||
keyuser <SSH Key User> | |||
keyhost <SSH Key Host> | |||
[Examples] | |||
set sshkey import copypaste | |||
Import public key in OpenSSH format. | |||
set sshkey import copypaste format openssl keyuser sysadmin keyhost slm-pipe | |||
Import public key in OpenSSL format on host "slm-pipe" for | |||
the user "sysadmin". | |||
Delete imported SSH key: | |||
set sshkey delete keyuser <SSH Key User> keyhost <SSH Key Host> | |||
[Examples] | |||
set sshkey delete keyuser sysadmin keyhost slm-pipe | |||
Delete imported SSH public key on host "slm-pipe" for the user "sysadmin". | |||
Display imported SSH keys: | |||
show sshkey import <one or more parameters> | |||
Parameters: [keyuser <SSH Key User>] | |||
[keyhost <SSH Key IP Address or Name>] | |||
[viewkey <enable|disable>] | |||
[Examples] | |||
show sshkey import | |||
Display all imported SSH public keys. | |||
show sshkey import viewkey enable | |||
Display all imported SSH public keys with content of keys. | |||
show sshkey import keyuser sysadmin keyhost slm-pipe | |||
Display imported SSH public key on host "slm-pipe" for the user "sysadmin". | |||
[sysadmin@192.168.1.96]> set user ? | |||
User Command Synopsis | |||
--------------------- | |||
Configure user information: | |||
set user add|edit <User Login> [<parameters>] | |||
Parameters: [email <Email Address>] | |||
[fullname <Full Name>] | |||
[group <Group Name|default|Admin|None>] | |||
[mobile <Phone Number>] | |||
set user delete <User Login> | |||
set user password <User Login> | |||
Note: The group 'default' (Unknown) and 'Admin' and are built-in groups. | |||
The group 'None' indicates that user is created without | |||
defining a group, and permissions will be assigned specifically | |||
to the user. A user will be assigned 'default' group by | |||
omitting group parameter when creating a new user. | |||
Display user information: | |||
show user name [user <User Login>] | |||
show user [index <Index Number>] | |||
# This is a PAID function that is not enabled on this device | |||
[sysadmin@192.168.1.96]> set vip ? | |||
Error: function 'cliHelpSetDna' not found. | |||
</pre> | |||
Latest revision as of 16:45, 12 September 2025

Details
Nice KVM over IP with USB port for remotely connecting virtual media. The current price as of 2021-02-05 is $559 although I think I got it for less than that years ago. There are more and cheaper solutions out there today, but this still works.
Modern Open Source Alternatives
For a long time there were no alternatives to devices like this, but now finally there's a cheap DIY project that can accomplish the same thing for much cheaper: Pi-KVM Project (Open and cheap DIY IP-KVM based on Raspberry Pi). It only costs between $30 and $100 for parts!
Resources:
- Pi-KVM - DIY CHEAP Raspberry Pi KVM over IP Prototype Version 3 Review! on YouTube
- Pi-KVM - Raspberry Pi Zero W Installation and Review on YouTube
Firmware
On 2020-06-30, version: 4.2.0 (Build 38135) was released. I have confirmed that this version supports the HTML 5 KVM mode.
- See release notes here: spider-v4.2-38135_2020-06-30-release_notes.txt
- Download here: spider-v4.2-38135_2020-06-30.zip
On 2020-02-26, version: 4.1.2 (Build 38134) was released. The release notes imply that this version supports the HTML 5 KVM mode but I have not tested it.
- See release notes here: spider-v4.1-38134_2020-02-26-release_notes.txt
- Download here: spider-v4.1-38134_2020-02-26.bin
On 2019-05-15, version 3.00.31 (Build 38120) was released. This version did not support HTML 5 KVM mode.
- See release notes here: spider-v3.0-38120_2019-05-15-release_notes.txt
- Download here: spider-v3.0-38120_2019-05-15.bin
On 2018-12-17, version 04.00.08 (Build 38118) was released. This was the first version to support HTML 5 KVM mode, but the download was taken down from the Lantronix website shortly afterwards. See this reddit thread for details. Nobody really knows what, if anything, is wrong with this firmware. It has been made available by a third party for posterity. The links below are not directly provided by Lantronix.
- See release notes here: spider-v4.0.8-38118_2018-12-17_User_Release_Notes.txt
- Download here: spider-v4.0.8-38118_2018-12-17.bin
Installing an SSL certificate
Unfortunately, this little appliance doesn't allow you to simply upload an SSL certificate. Rather, you need to create a certificate signing request (CSR) and send that to your SSL certificate provider / authority.
Step 1: Generate a certificate signing request on the Spider Duo portal. If your hostname for your lantronix spider duo is spider, you would go here: https://spider/cert.asp
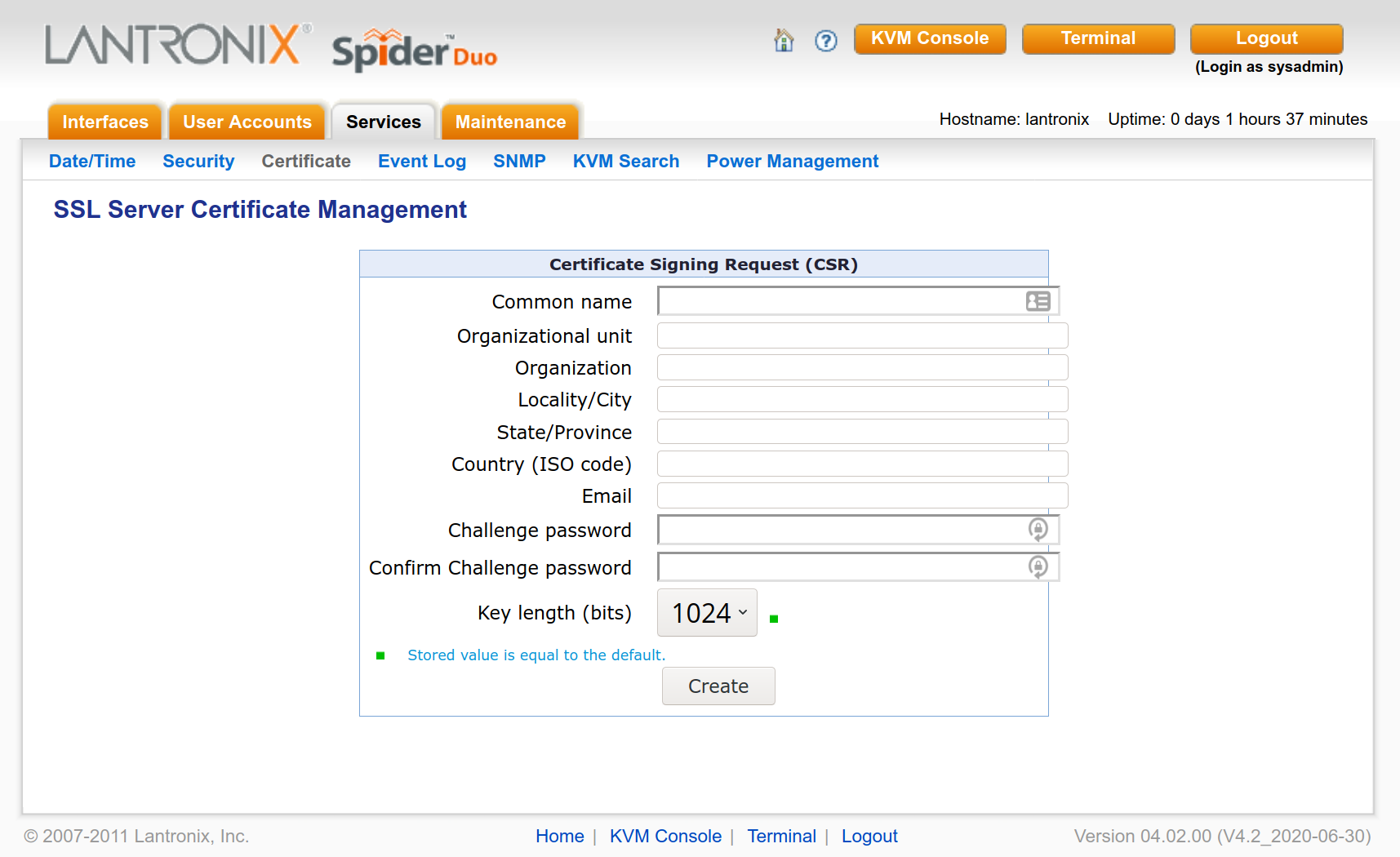
Fill out all fields and change the key length to the highest available (currently only 2048). Then click the "Create" button.
Step 2: Download the CSR file and save to csr.txt
Step 3: Use the certbot tool to create the certificate. This will require validation of the fact that you control the domain (common name) of the certificate. In this example, I use the webroot option and the common name of the certificate is certificate-example.mydomain.com:
jeremy@latitude /tmp/cert $ DIR_CONFIG=./config jeremy@latitude /tmp/cert $ DIR_WORK=./work jeremy@latitude /tmp/cert $ DIR_LOGS=./logs jeremy@latitude /tmp/cert $ mkdir $DIR_CONFIG $DIR_WORK $DIR_LOGS jeremy@latitude /tmp/cert $ certbot certonly --cert-path cert.pem --key-path key.pem --csr csr.txt --config-dir $DIR_CONFIG --work-dir $DIR_WORK --logs-dir $DIR_LOGS Saving debug log to /tmp/cert/logs/letsencrypt.log How would you like to authenticate with the ACME CA? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: Spin up a temporary webserver (standalone) 2: Place files in webroot directory (webroot) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Plugins selected: Authenticator webroot, Installer None Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): youremail@mailprovider.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: N Performing the following challenges: http-01 challenge for certificate-example.mydomain.com Input the webroot for certificate-example.mydomain.com: (Enter 'c' to cancel): /var/www/html Waiting for verification... Cleaning up challenges Server issued certificate; certificate written to /tmp/cert/cert.pem Cert chain written to 8 Cert chain written to 9
Step 4: Upload the cert.pem file to the Spider Duo portal.
Step 5: Rest easy that there's no man in the middle.
SSH Access
sysadmin@192.168.1.96's password:
Welcome to the Lantronix SLSLP
Firmware: version 040200, build 38135
Last login: Thu Jan 1 12:18:43 1970 from 192.168.1.109
Current time: Thu Jan 1 21:43:54 1970
For a list of commands, type 'help'
[sysadmin@192.168.1.96]> help
SLS Command Line Help
---------------------
For more information on a command, type 'help <command>'
For example, 'help show history'.
For general CLI help, type 'help command line'.
set datetime|device|group|history|network|oem|power|security|serial|
sshkey|user|vip
show datetime|device|group|history|network|oem|power|security|serial|
sshkey|sysconfig|user|vip
connect serial|wakeonlan
diag ping|ping6
usbhost disk
admin config|reboot|reset|version
logout terminates CLI session
[sysadmin@192.168.1.96]>
[sysadmin@192.168.1.96]>
[sysadmin@192.168.1.96]> set datetime ?
Date/Time Command Synopsis
--------------------------
Set the date/time or UTC offset:
set datetime <one parameter>
Parameters: date <MMDDYYhhmm[ss]>
utcoffset <offset string>
MMDDYYhhmm[ss]:
MM: 1-12 DD: 1-31 YY: 00-99
hh: 0-23 mm: 0-59 ss: 0-59
Offset string:
-11h, -10h, -9h, -8h, -7h, -6h, -5h, -4h, -3h, -2h, -1h,
+/-0h,
+1h, +2h, +3h, +4h, +5h, +6h, +7h, +8h, +9h, +10h, +11h, +12h.
(Note: Select only one offset as shown above)
Show the date/time and UTC offset:
show datetime
[sysadmin@192.168.1.96]> set device ?
Device Command Synopsis
---------------------
Display device information:
show device
show device all
show device name [name <Device Name>]
show device [index <Index Number>]
Configure device information:
set device add|edit <Device Name>
macaddress <MAC Address>
[<parameters>]
Parameters: ipaddress <IP Address>
password <Password>
MAC address must be in hex format: 'XX:XX:XX:XX:XX:XX'
set device delete <Device Name>
[sysadmin@192.168.1.96]> set group ?
User Group Command Synopsis
---------------------------
Configure user group for users who login to SLS.
set group add|edit <Group Name> [<parameters>]
set group delete <Group Name>
Parameters: permissions <Permission List>
Note: See 'help group permissions' for information on groups rights.
Display group information:
show group [name <Group Name>]
show group [index <Index Number>]
Note: [Group of 'None (username)'] indicates that user was created
without defining a group, and permissions will be assigned
specifically to the user. In order to specify a group of
this type "None", use '@username' as the name parameter.
[sysadmin@192.168.1.96]> set history ?
History Command Synopsis
------------------------
Clears the CLI command history:
set history clear
Displays the 100 most recent CLI commands:
show history
[sysadmin@192.168.1.96]> set network ?
Network Command Synopsis
------------------------
Configures network setting:
set network basic <parameters>
Parameters:
dns1 <IP Address>
dns2 <IP Address>
gateway <IP Address>
hostname <Host Name>
ipaddr <IP Address>
ipv6 <enable/disable>
ipv6addr <IPv6 Address/Prefix>
mask <Mask>
state <dhcp|bootp|static>
set network misc <parameters>
Parameters:
bwlimit <8-10000 kbit/s>
httpsports <TCP Port>
httpport <TCP Port>
proxy <enable/disable>
proxyhost <IP Address>
proxyport <TCP Port>
telnet <enable/disable>
telnetport <TCP Port>
setupprotocol<enable/disable>
ssh <enable/disable>
sshport <TCP Port>
set network interface <parameters>
Parameters:
mode <auto|10mbit-half|100mbit-half|10mbit-full|100mbit-full>
Display network parameter settings.
show network all
show network basic
show network misc
show network interface
To clear IPV4 address, set ipv4 address to '0.0.0.0'
To clear IPV6 address, set ipv6 address to '::' or '::/128'
[sysadmin@192.168.1.96]> set oem ?
OEM Customization Command Synopsis
----------------------------------
Configure OEM customization parameters.
Change product/company specific information on the web interface.
Set OEM parameters:
set oem <one or more parameters>
Parameters: [product <Product Name>]
[company <Company Name>]
[copyright <Copyright>]
[url <URL>]
[title <Title>]
[Examples]
set oem product MyKVM company MyCompany
Set product name 'MyKVM' and company name 'MyCompany'
Display OEM settings:
show oem
[sysadmin@192.168.1.96]> set power ?
Power Command Synopsis
----------------------
Configure Power Control Unit (PCU) parameters.
Set PCU parameters:
set power <parameters>
Parameters: [state <on/off>]
Display Power Control Unit status and settings:
show power
[sysadmin@192.168.1.96]> set security ?
Security Command Synopsis
-------------------------
Set security parameters:
set security <one or more parameters>
Parameters: [forcehttps <enable|disable>]
[singlelogin <enable|disable>]
[kvmencryption <off/try/force>]
[screenshot <enable|disable>]
[directkvm <enable|disable>]
Show security settings.
show security
[sysadmin@192.168.1.96]> set serial ?
Serial Port Command Synopsis
----------------------------
Set active serial mode:
set serial mode passthrough
set serial mode config
Set serial port parameters for each mode:
set serial mode passthrough|config [<parameters>]
Parameters: [baud <300-115200>]
[databits <7|8>]
[stopbits <1|2>]
[parity <none|odd|even>]
[flowcontrol <none|xon/xoff|rts/cts>]
Show serial port settings
show serial
[sysadmin@192.168.1.96]> set sshkey ?
SSH Key Command Synopsis
------------------------
Import SSH key (OpenSSH format):
set sshkey import <copypaste>
Note: RSA keys must be 1024 bits.
Import SSH key (OpenSSL format) :
set sshkey import <copypaste> format <openssl>
keyuser <SSH Key User>
keyhost <SSH Key Host>
[Examples]
set sshkey import copypaste
Import public key in OpenSSH format.
set sshkey import copypaste format openssl keyuser sysadmin keyhost slm-pipe
Import public key in OpenSSL format on host "slm-pipe" for
the user "sysadmin".
Delete imported SSH key:
set sshkey delete keyuser <SSH Key User> keyhost <SSH Key Host>
[Examples]
set sshkey delete keyuser sysadmin keyhost slm-pipe
Delete imported SSH public key on host "slm-pipe" for the user "sysadmin".
Display imported SSH keys:
show sshkey import <one or more parameters>
Parameters: [keyuser <SSH Key User>]
[keyhost <SSH Key IP Address or Name>]
[viewkey <enable|disable>]
[Examples]
show sshkey import
Display all imported SSH public keys.
show sshkey import viewkey enable
Display all imported SSH public keys with content of keys.
show sshkey import keyuser sysadmin keyhost slm-pipe
Display imported SSH public key on host "slm-pipe" for the user "sysadmin".
[sysadmin@192.168.1.96]> set user ?
User Command Synopsis
---------------------
Configure user information:
set user add|edit <User Login> [<parameters>]
Parameters: [email <Email Address>]
[fullname <Full Name>]
[group <Group Name|default|Admin|None>]
[mobile <Phone Number>]
set user delete <User Login>
set user password <User Login>
Note: The group 'default' (Unknown) and 'Admin' and are built-in groups.
The group 'None' indicates that user is created without
defining a group, and permissions will be assigned specifically
to the user. A user will be assigned 'default' group by
omitting group parameter when creating a new user.
Display user information:
show user name [user <User Login>]
show user [index <Index Number>]
# This is a PAID function that is not enabled on this device
[sysadmin@192.168.1.96]> set vip ?
Error: function 'cliHelpSetDna' not found.